Let’s discuss Intune support for Multi-Session Windows Server OS version Windows 11 or Windows 10 multi-session. Intune support is there only for a server opening system called multi-session. The Intune support for the rest of the server operating system is still not there.
Intune support is already available for Hybrid Azure AD, and Azure AD joined AVD (a.k.a Azure Virtual Desktop) VMs. Intune support for a Windows 11 or Windows 10 multi-session preview was announced a few months back.
In this post, let’s also discuss Ivanti Environment Manager and Citrix WEM requirements for the VDI server workload production deployment scenario (don’t forget to check out the Conclusion section).
Microsoft announced the general availability of Intune support for multi-session in April 2022. Windows 10 or Windows 11 multi-session VM’s Intune management is out of public preview now. It’s not recommended to use the same policies for multi-session and single-session workloads in AVD.
More details on policy creation for multi-session are discussed in the following sections. This means all the user-based policies are not supported for the multi-session scenarios. So, it would be best if you were careful while creating Intune policies for multi-session scenarios.
The tag line here with Intune management of multi-session VMs is you must use device-based configurations wherever possible to support user-less enrollments. Windows 10 multi-session support is already in place for Configuration Manager (a.k.a SCCM). You can read more about SCCM Windows 10 or Windows 11 Multi-Session Support For AVD.
Prerequisites Multi-Session Support with Intune
I had tested multi-session when it was not in support at all. However, the following are prerequisites for a supported scenario for multi-session Windows 11 or Windows 10 management with Intune.
- Windows 10 multi-session, version 1903 or later.
- Or Windows 11 multi-session.
- Hybrid Azure AD-joined (Domain Join + Azure AD Registered).
- Or Azure AD Join.
- AVD agent version of 1.0.2944.1400 or later.
- Enrolled in Intune using any of the following options:
- Use Active Directory group policy (for Hybrid Azure AD Join scenario), set to use Device credentials.
- SCCM co-management to enroll in Endpoint Manager Intune (MEM).
- Intune enrollment with multi-session VMs using AVD provisioning workload.
Overview of Multi-Session Management with Intune
Let’s check the overview of Multi-Session Management with Intune. You can check the supported policy details in the below section.
#1 You need to remember that the user policies are applied only after the user’s first log in (as expected). I don’t think it won’t take more than 2 minutes to apply security policies to the VM after the user first login. This is the same experience with a single session.
#2 Use device-based Intune policies wherever possible to speed up the user enrollment process, as explained in the above link. User-based policies must be deployed to Azure AD user groups, and device-based policies must be deployed to Azure AD Device groups. While writing this post, only device policies are supported.
- #3 What is enrolment time in this context – the time between the first login (when the user gets to see the desktop) to a non-persistent (even applicable for persistent) multi-session VM and the VM is ready for the user to use after applying all the security policies and apps.
#4 Critical User Policy for multi-session scenarios – There are some user policies that should be applied immediately after login; otherwise, outlook auto-discovery or configurations won’t get loaded properly.
- #5 Use Intune Settings Catalog for multi-session VMs– The existing device configuration profile templates aren’t supported for Windows 10 or Windows 11 multi-session VMs, except Trusted Certificates, SCEP Certs, PKCS, and VPN (device tunnel).
#6 Intune won’t deliver unsupported templates to multi-session devices, and those policies appear Not applicable in reports.
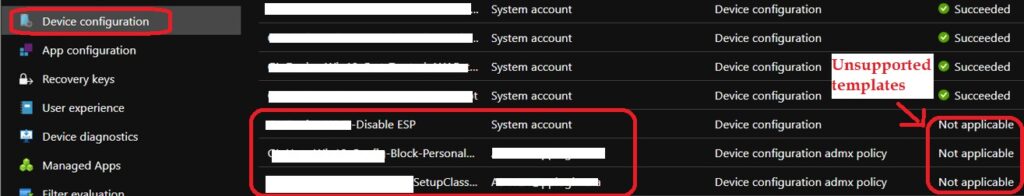
#7 – ADMX-ingested policies are supported with multi-session, including Office and Microsoft Edge settings available in Office administrative template files and Microsoft Edge administrative template files. Some of the ADMX-ingested policies are not applicable for multi-session.
- #8 – Only device-based compliance policies are now supported by Windows 10 or Windows 11 multi-session VMs. The user or device-based Conditional Access Policies are supported for multi-session VMs.
Multi-Session Server OS Policy Deployment Using Intune
As discussed in the overview section above, most default policy templates are not supported for multi-session scenarios. So, you are allowed to reuse the existing policies created using unsupported templates. Only the certificate templates are supported for multi-session, as explained above.
Windows 10 or Windows 11 Multi-Session policy creation and deployment must use Intune settings catalog or ADMX injection templates as mentioned in the overview section. Let’s check how to create the Multi-Session server OS policy using Intune.
- Sign in to endpoint.microsoft.com.
- Navigate to Devices > Windows > Configuration profiles.
- Click on Create Profile.
- Select Platform: Select Windows 10 and later.
- Profile: Select Settings catalog.
Click on the Create button to continue to the next page.
You can enter the details such as the name of the Policy and settings on the below screens. The multi-Session policy is being created now. I recommend specifying the scenario and user/device-based policy in the name itself.
- Enter the Name of the Multi-Session user-based policy – AVD-Multi-Session-User-Policy-ControlPanel-Settings.
- Enter the Description of the policy.
- Click on the Next button to continue.
You can click on the +Add Settings link to bring up the new blade of the policy configuration wizard. This link will help with a new blade called the Settings Picker with a search box.
Settings catalog – You can choose which settings you want to configure with the settings catalog. Click on Add settings to browse or search the catalog for the settings you want to configure.
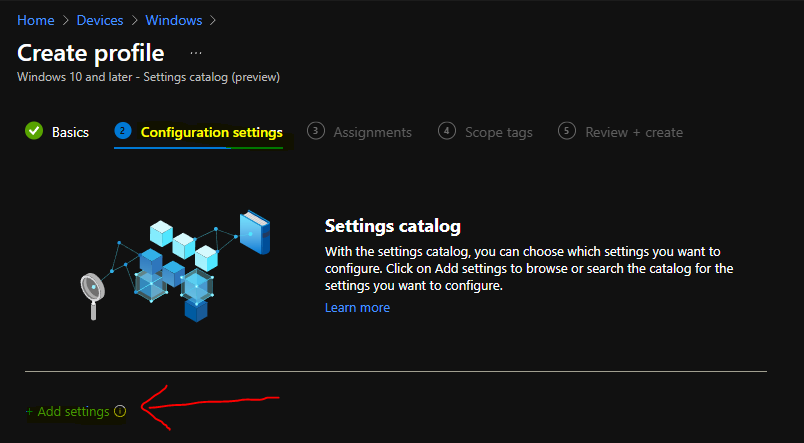
- Under Settings picker, click on Add filter and select the following options:
- Key: OS edition
- Operator: ==
- Value: Enterprise multi-session
Click on Apply button to show the filtered list of all configuration profile categories that support Windows 10 or Windows 11 multi-session. You can see the scope for the policy in parentheses (Device or User).
NOTE! – While writing this post, only device settings are supported for multi-session. However, in this post, I try to deploy some user-based policies for testing. I don’t recommend trying this out.
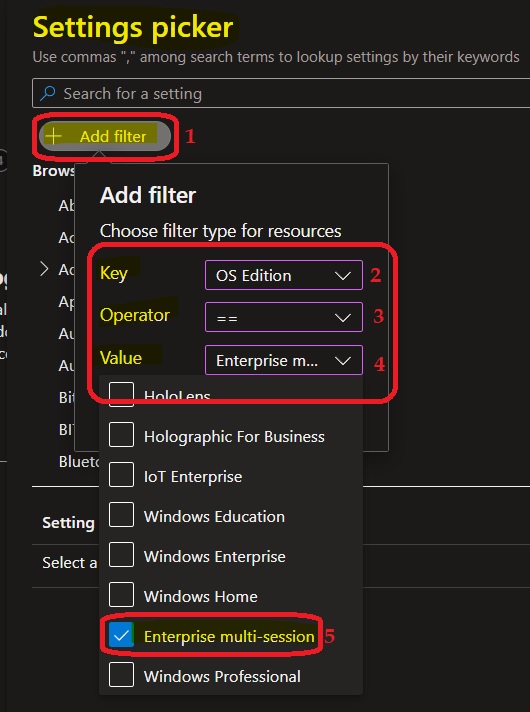
I used the keyword “Control panel” to filter down the policy results further. Remember, I have already filtered down for a multi-session OS version.
The following are the 4 settings available for the Control panel settings available for the Multi-session scenarios. All those 4 settings are user-based policies, so they must be deployed to the Azure AD User Group.
- Always open All Control Panel Items when opening Control Panel (User)
- Hide specified Control Panel items (User)
- Prohibit access to Control Panel and PC settings (User)
- Show only specified Control Panel items (User)
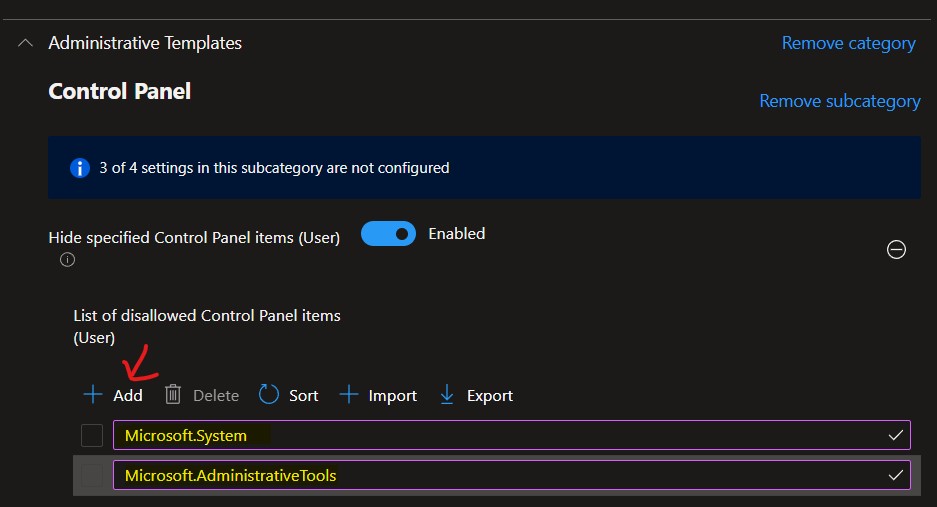
I have selected a user-based setting called Hide specified Control Panel items (User).
Enable the policy by using the toggle button, as shown in the screenshot below.
- Click on the +Add button to add the control panel canonical names to hide those settings from the control panel.
- Click on the Next button to continue.
The System and Administrative Tools will be hidden from the control panel once this policy is successfully implemented.
You must use the Azure AD User group to assign this policy deployment. You can use Intune filters from the assignment page to filter out devices that are not required (single session and physical).
You can click on the Next button and add the Scope Tags on the next page. You will need to click on the next and create buttons to complete the policy creation process.
I have explained how to build an Intune filter rule for multi-session devices in the following blog post. More details – AVD Intune Support Is Available For Windows 10 Or Windows 11 Multi-Session.
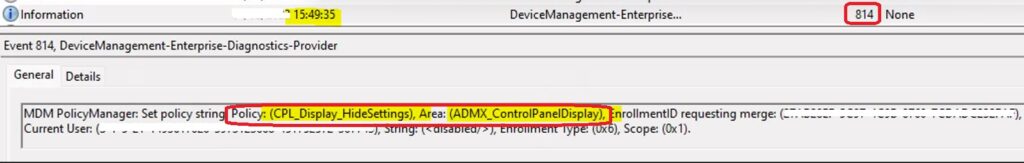
Event Logs – Intune Support for Multi-Session Windows Server OS
I see the policies are applied to the user immediately after the login, which is really nice from the event logs. You can check event logs of multi-session VM to get more details. I see some gotchas with the user policy deployments, which are covered in this post’s summary section.
Intune log (event) path is the Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
More Details – Intune Logs Event IDs Registry Entries For Windows Client Side Troubleshooting.
Endpoint Security Platform Supports Windows Server?
Let’s check whether the Endpoint Security Platform Supports Windows Server? This supports Windows 10 or Windows 11 multi-session VMs.
- Log in to the endpoint.microsoft.com portal.
- Navigate to Endpoint Security -> Endpoint detection and response.
- Click on Create Policy to create the Endpoint security policy for Multi-Session VMs.
Microsoft Defender for Endpoint endpoint detection and response capabilities provide advanced attack detections near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
Intune Application Deployment for Multi-Session VMs
You can deploy the application to multi-session VMs if the application is installed in the System or Device context. There is no support to deploy web applications because they always get installed in the user context.
The available deployment is not supported for multi-session VMs. Also, AVD Remote Apps and MSIX app attach are not supported for Intune application deployment scenarios.
PowerShell Script Deployment for Multi-Session VMs
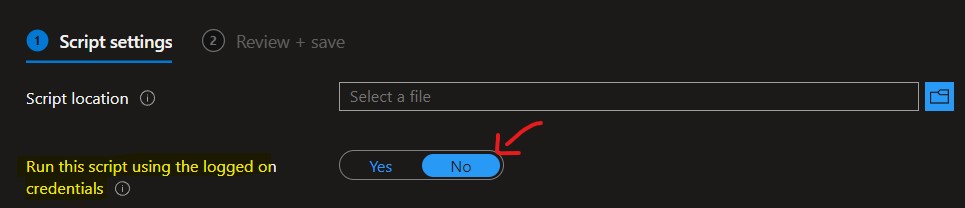
Let’s check options for PowerShell Script Deployment for Multi-Session VMs with Intune. While writing this post, you can deploy the PowerShell script only in System Context. The setting called Run this script using the logged on credentials must be set to No.
Patching Policies for Multi-Session VMs
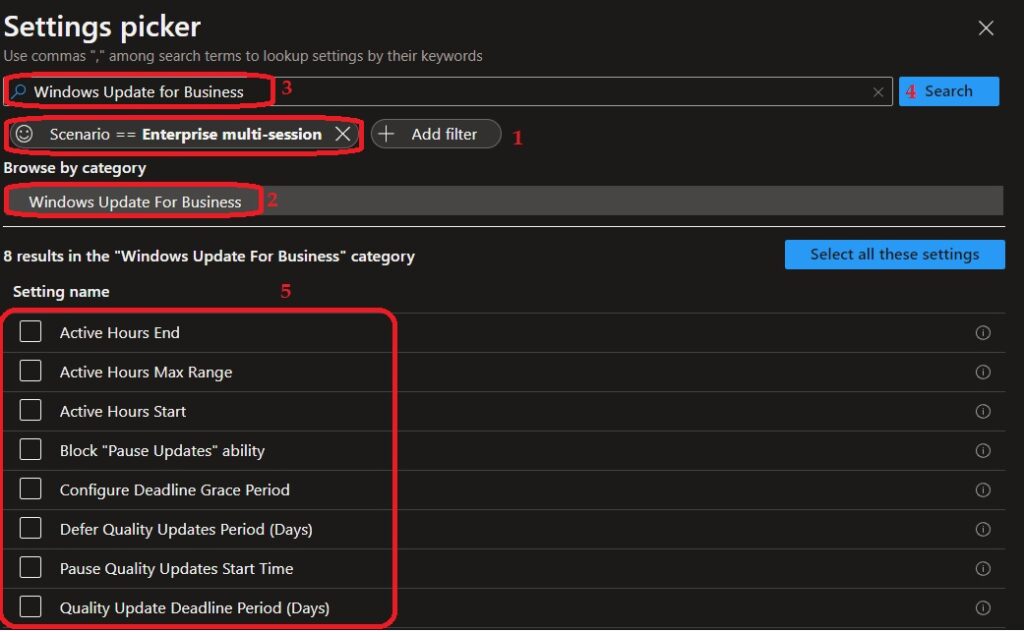
Let’s check the Software Updates or Patching Policies for Multi-Session VMs. You have to use the Settings Catalog Windows Update for Business option for WUfB policies. There are only 8 WUfB supported policies for Windows 11 or Windows 10 multi-session VMs.
You need to filter the setting catalog based on OS edition as explained in the above section and then search with the keyword “Windows Update for Business” to get the results that you can see in the screenshot below.
- Active Hours End
- Active Hours Max Range
- Active Hours Start
- Block “Pause Updates” ability
- Configure Deadline Grace Period
- Defer Quality Updates Period (Days)
- Pause Quality Updates Start Time
- Quality Update Deadline Period (Days)
Intune Remote Actions Support for Multi-Session VMs
Let’s check Intune Remote Actions Support for Multi-Session VMs. More details on Remote actions on Device Actions using Intune. While writing this post, the following 6 remote actions are not supported for multi-session VMs.
- Autopilot reset
- BitLocker key rotation
- Fresh Start
- Remote lock
- Reset password
- Wipe
Conclusion | Intune Support for Multi-Session Windows Server OS Version | AVD Workloads
The User-based policy deployments using the settings catalog are not supported yet. This is mandatory for production deployment of AVD multi-session with Intune management. Let’s have a quick summary of Intune Support for Multi-Session Windows Server OS.
Avoiding user-based policies in production AVD deployment is not quite feasible in my experience, even though Microsoft recommends avoiding user-based policies. User-based policies and control are essential for AVD multi-session deployments.
- #1 – I have seen organizations using Ivanti Environment Manager (powered by Appsense) or Citrix WEM to get complete control over the user-based policy deployment for server-based workloads such as Server 2019 and 2022 Citrix Cloud VDAs.
#2 – It’s great news that Microsoft is taking baby steps toward Windows 11 or Windows 10 multi-session support with user policies in the coming days. However, I feel it would be difficult to rely only on Intune multi-session support for the production deployment of server workloads such as multi-session now.
- #3 – I have not seen any Windows 11 or Windows 10 multi-session support statement for Ivanti Environment Manager. It seems Citrix WEM already supports Windows Multi-Session operating system.
You would be able to Deploy Multi-Session Windows 11 or Windows 10 Workloads to an on-prem datacenter using Azure Stack HCI implementation. More details are available – On-Prem Azure Virtual Desktop With Azure Stack HCI.
