PowerShell Script to Track Upcoming Microsoft Entra App Secret Expirations! In this article, I’ll walk you through a powerful automation designed to enhance proactive security and lifecycle management for Microsoft Entra applications. You’ll learn how to monitor Entra app registrations and automate the detection of upcoming secret key expirations, ensuring your identity infrastructure stays secure and well-maintained.
Microsoft Entra ID, formerly known as Azure Active Directory is a modern, cloud-native solution for identity and access management. As a robust directory and identity service, it delivers a comprehensive set of authentication and authorization capabilities across Microsoft services such as Office 365, Dynamics 365, Azure, and a wide range of cloud-based applications.
From an administrative standpoint, Microsoft Entra ID offers a powerful framework for identity and access management. Administrators can govern access to applications and resources with precision, leveraging Entra ID to implement granular policies that ensure only authorized users can interact with specific assets. This level of control strengthens organizational security and supports compliance across cloud environments.
Microsoft Entra ID serves as a standards-based authentication provider, enabling app developers to integrate single sign-on (SSO) using users’ existing credentials. This streamlines access across applications while enhancing security and user experience. Additionally, developers can leverage Microsoft Entra APIs to tap into organizational data, allowing them to build rich, personalized experiences tailored to enterprise environments.
Table of Contents
PowerShell Script to Track Upcoming Microsoft Entra App Secret Expirations – Know More about Microsoft Entra ID app registration
Microsoft Entra ID app registration is generally used by developers who work with the Entra ID platform and get access using user accounts and groups. Those accesses are based on one or more API permissions in Entra apps.
Registering an application in Microsoft Entra creates a unidirectional trust relationship between the app and the Microsoft identity platform. In this setup, the application trusts the identity platform to authenticate users and manage access, but the platform does not inherently trust the app. This trust is scoped to the tenant where the app is registered, and once the application object is created, it cannot be transferred to another tenant!

- Top 5 Security Layers of Protection
- Block Users Personal Devices to Join Entra ID using Intune
- External Collaboration Settings in Entra ID
- Best Guide To Configure App Registration In Microsoft Entra
Most Entra App registrations are created to access resources or APIs, such as Microsoft Graph, SharePoint, or custom APIs. In these cases, API permissions must be granted, either delegated (on behalf of a user) or application-level (without user context). If you’re registering an app purely for authentication (e.g., enabling SSO for a web app), you might not assign API permissions at first.
Roles Required to Manage Entra App Registration
To create or manage Microsoft Entra app registrations, you need specific roles and API permissions depending on the scope of your tasks. Let’s discuss the roles that required to manage Microsoft Entra App registartion.
| Role | Description |
|---|---|
| Application Administrator | Full control over all aspects of app registrations, including secrets, certificates, API permissions, and redirect URIs |
| Cloud Application Administrator | Can create and manage app registrations, but with slightly narrower scope than Application Administrator. Also able to grant admin consent for delegated permissions |
| Privileged Role Administrator | Can assign roles to users, including the above roles. Needed if you’re managing access control for app management. |
| Application Developer | Users in this role can create application registrations when the “Users can register applications” setting is set to No. |
- Microsoft Cloud LAPS Password Management Solution
- Get Microsoft Defender for Endpoint Product Comparison and License Assignment Options
How to Check Microsoft Entra App Secret Expiry Date Manually
The Microsoft Entra app secret expiry date is defined at the time of secret creation. By default, the expiration is set to 180 days, but administrators can choose from several predefined options such as 90, 365, 545, or 730 days, or specify a custom duration based on organizational requirements.
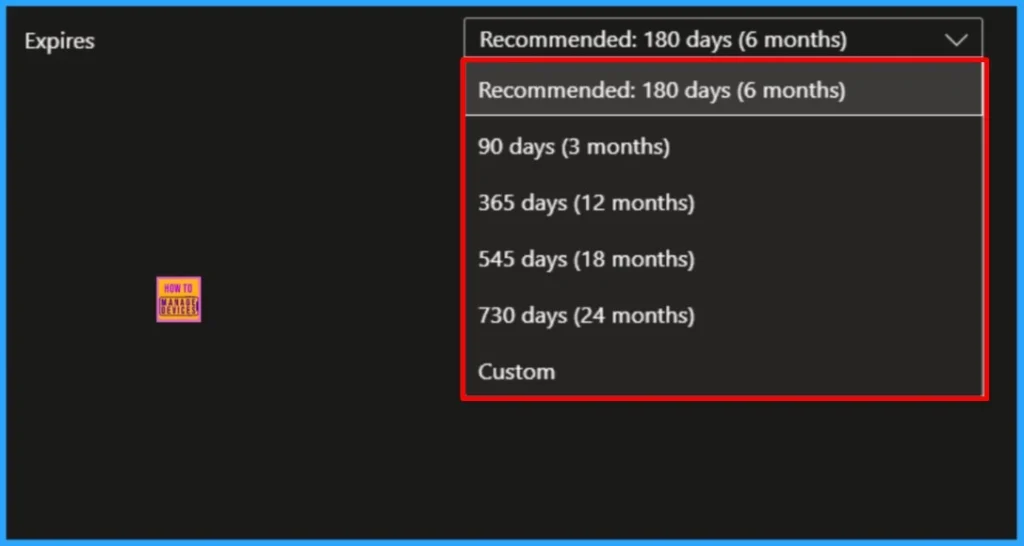
Before automating Microsoft Entra app secret expirations, it’s important to understand how to manually check the expiry date of an app secret. Let me walk you through the process.
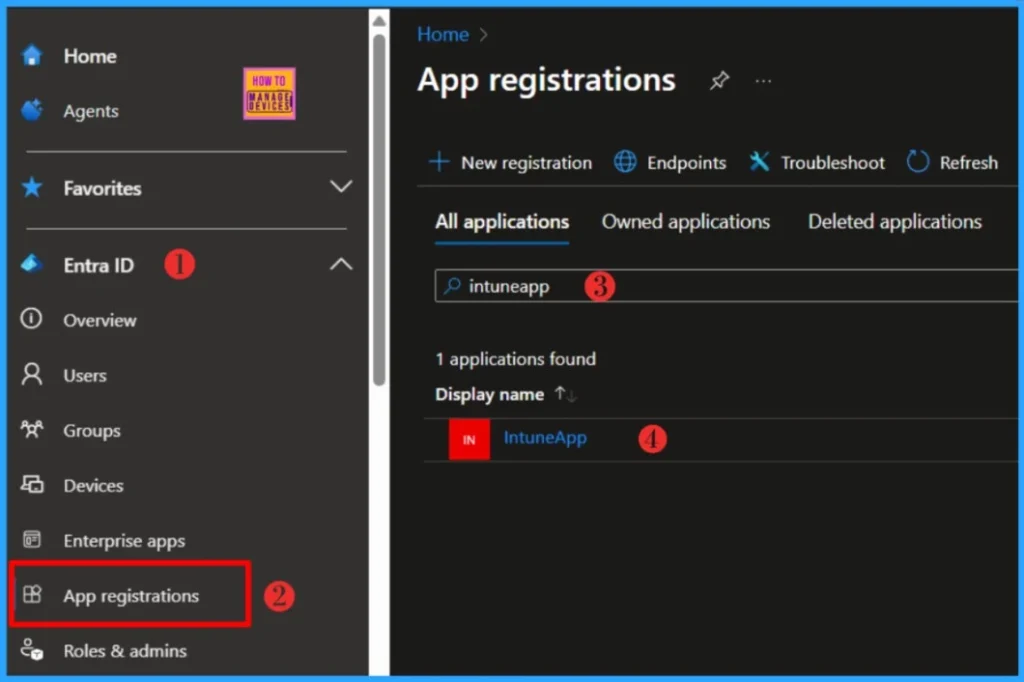
- Sign in to the Microsoft Entra admin center
- Expand Entra ID and select App registrations
- Search for the application you want to check the secret expiry date for.
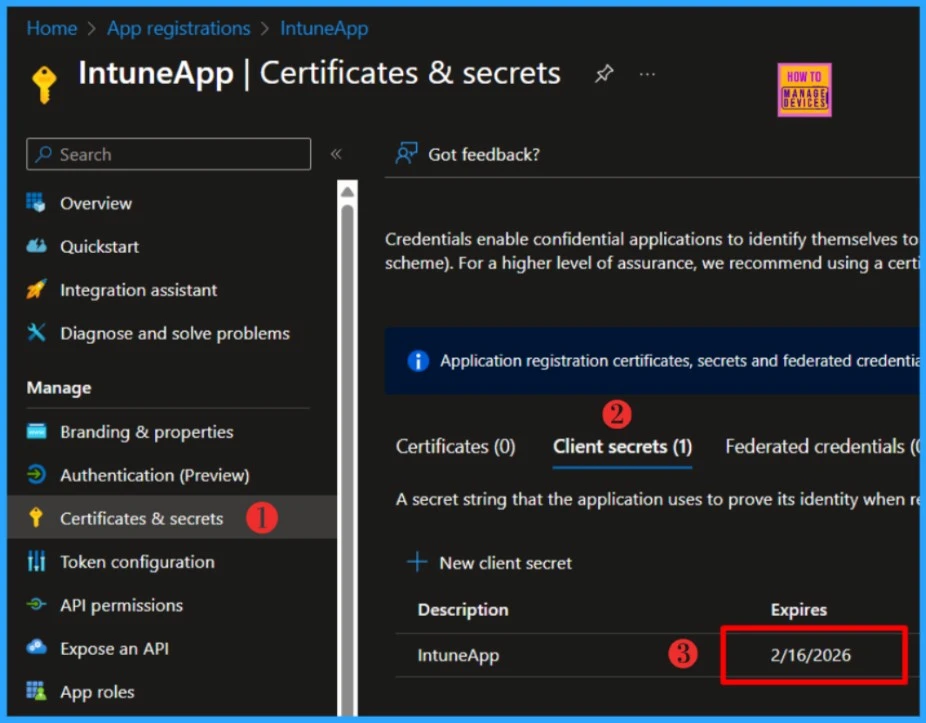
Click on the application whose secret expiry date you want to check. In the Overview tab, you’ll find key identifiers such as the Client ID, Object ID, and Tenant ID. To view the secret’s expiry date, navigate to the Certificates & Secrets section of the app registration. Under the Client Secrets tab, you’ll find the expiration date listed alongside each secret.
- Easiest Method to Enable MFA for Admins using Azure AD Conditional Access
- What is the Face Check Feature in Entra
- Windows 10 Conditional Access with Azure AD Join Intune MDM Auto Enrollment Enforce Policies
PowerShell Script to Check Microsoft Entra App Secret Expiry
We’ve learned how to manually check the expiry date of Microsoft Entra app secrets. However, reviewing each secret daily isn’t feasible. An automated solution is essential to save time, reduce risk, and improve operational efficiency.
NOTE! Use the Connect-MgGraph command to sign in with the required scopes. You'll need to sign in with an admin account to consent to the required scopes.- Best Guide to Install Microsoft Graph PowerShell Modules
- Complete Guide to Install the New Microsoft Entra PowerShell Module
- How to Pause Intune Config Refresh Feature on Windows Device using Microsoft Graph API
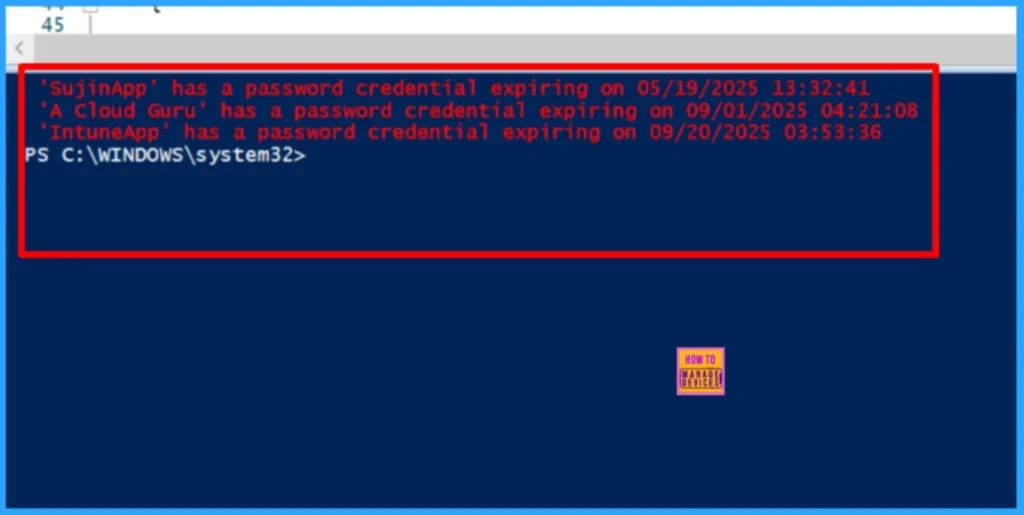
The following script checks all registered applications in Microsoft Entra (via Microsoft Graph) and identifies any password credentials (client secrets) that are set to expire within the next 30 days.
##########################################################################
#Get-EntraAppExpiryDate.ps1
#Author : Sujin Nelladath
#LinkedIn : https://www.linkedin.com/in/sujin-nelladath-8911968a/
##########################################################################
cls
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "Application.Read.All" -NoWelcome
# Define expiration threshold
$thresholdDate = (Get-Date).AddDays(30)
$expiringApps = @()
try {
$applications = Get-MgApplication
foreach ($app in $applications)
{
foreach ($credential in $app.PasswordCredentials)
{
if ($credential.EndDateTime -and $credential.EndDateTime -lt $thresholdDate)
{
$expiringApps += [PSCustomObject]@{
DisplayName = $app.DisplayName
ExpiryDate = $credential.EndDateTime
AppId = $app.AppId
}
}
}
}
if ($expiringApps.Count -gt 0)
{
foreach ($entry in $expiringApps)
{
Write-Host " '$($entry.DisplayName)' has a password credential expiring on $($entry.ExpiryDate)" -ForegroundColor Red
}
}
else
{
Write-Host " No application credentials are expiring within the next 30 days." -ForegroundColor Green
}
}
catch
{
Write-Host " An error occurred while retrieving application data: $($_.Exception.Message)" -ForegroundColor Yellow
}I have uploaded the PowerShell script to the my GitHub repository. You may access it from there for your further use.
Download: Get-EntraAppExpiryDateI trust that this article will significantly benefit you and your organization. I appreciate your patience in reading this post. I look forward to seeing you in the next post. Keep supporting the HTMD Community.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
About the Author: Sujin Nelladath, a Microsoft Graph MVP with over 11 years of experience in SCCM device management and Automation solutions, writes and shares his experiences with Microsoft device management technologies, Azure, DevOps and PowerShell automation.


