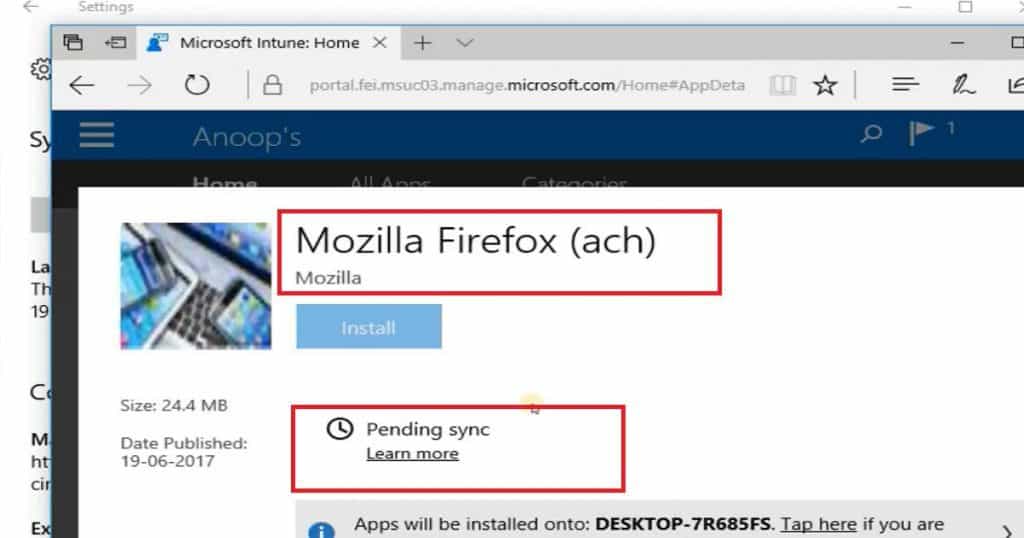
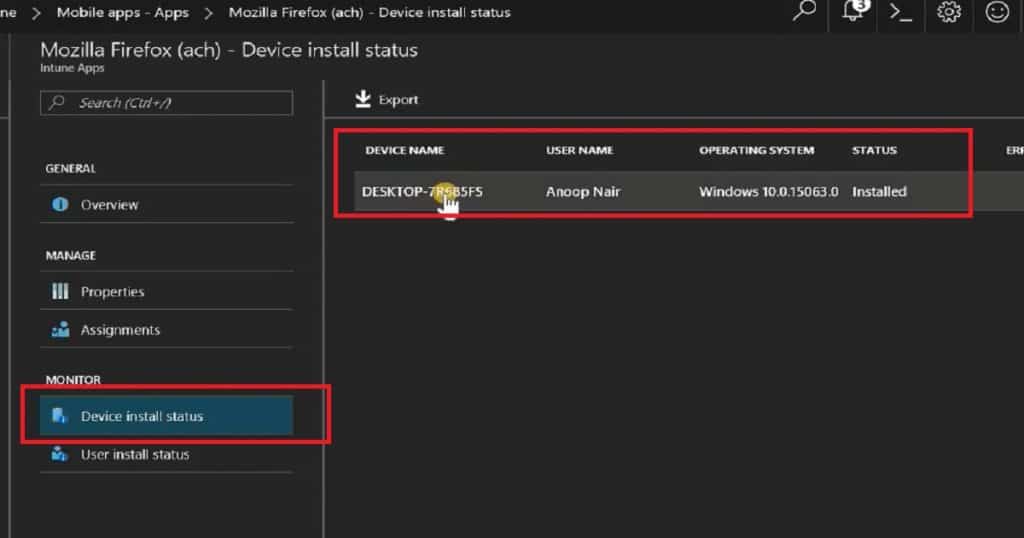
Let’s discuss Windows 10 Quality Feature Update Policies for Intune Step-by-Step Guide. Microsoft released Windows 10 1709, the fall Creators update. Devices in the current branch (Semi-Annual Targeted) should be updated in Settings—Update and Security—Windows Update.
Intune Windows 10 Quality Update Policies. Microsoft Intune manages this Windows 10 device. This post will see “Windows 10 1709 Fall Creators Update Upgrade with Intune Update Rings.”
Many methods exist to upgrade the Windows 10 version to the latest version, 1709. You can upgrade to Windows 10 with an ISO file available in Visual Studio Subscriptions (previously known as MSDN) or VLSC (Volume Licensing Service Center).
If Microsoft Intune manages your devices, a software update policy ring will manage Windows 10 feature updates.
Table of Contents

- Windows 10 Quality Vs Feature Updates – which is More Critical?
- Windows 10 21H2 Support is Ending in June
- Windows 10 and SCCM Patch Management (Windows 10 Quality Update Management) process
- Intune Quality and Feature Update Policies for Windows 10 devices]
Another Related Post on Windows 10 Update Rings
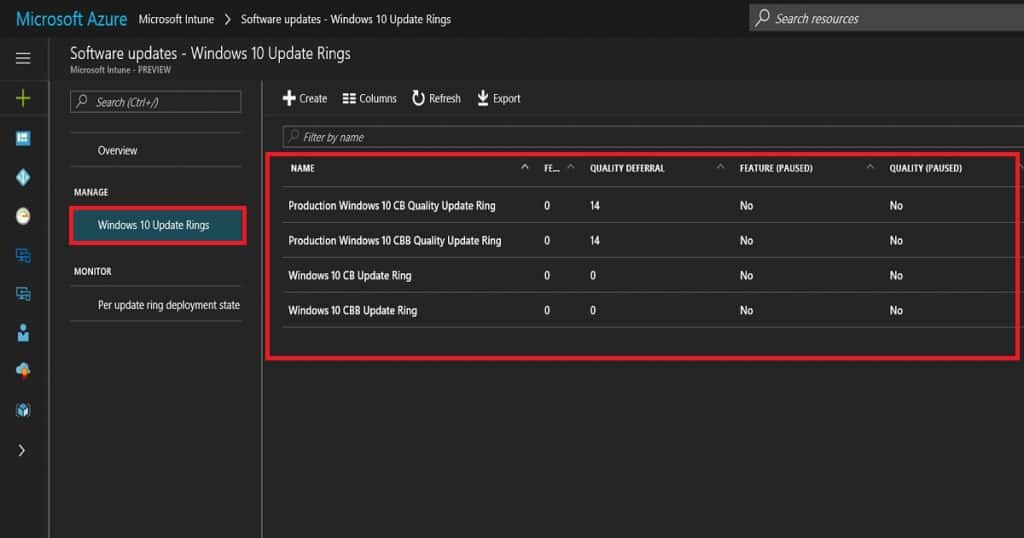
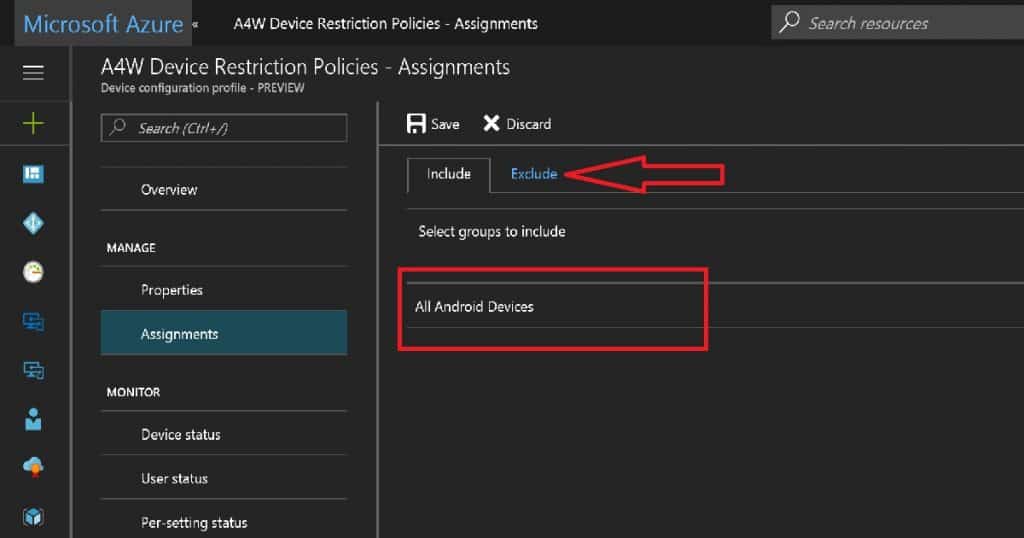
Navigate via Microsoft Azure—Microsoft Intune—Software Updates to “Windows 10 Update Rings.” Here, you can create Windows 10 Semi-Annual Targeted and Semi-Annual update rings.
These two update rings in Intune can control your organization’s Windows 10 upgrade behavior. Intune Windows 10 Quality Update Policies.
- Windows 10 Semi-Annual Targeted Update Ring – All the devices in the Current Branch.
- Windows 10 Semi-Annual Update Ring – All the devices in the Current Branch for Business
- FIX CBB Ring Devices are Getting CB Updates Intune Windows 10 Update Rings
- Windows 10 1709 Fall Creators Update Upgrade with Intune Update Rings
Create Windows 10 Update Rings in Intune?
In my previous posts, I explained the details of the Intune policy, “How to Setup Windows 10 Software Update Policy Rings in Intune Azure Portal.”
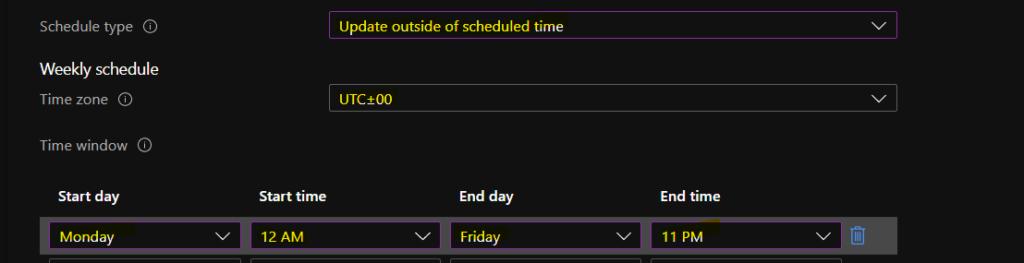
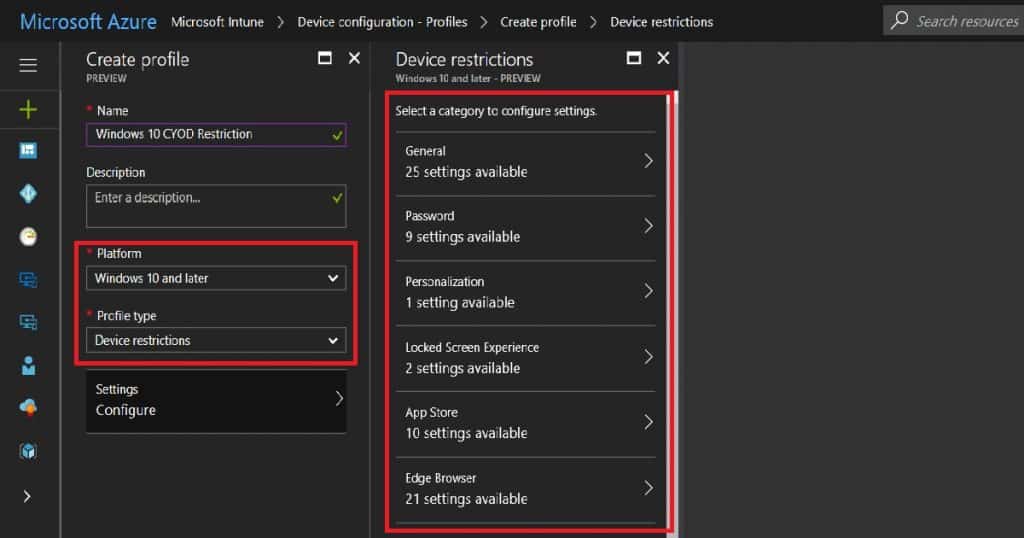
Navigate via the Intune console to access Windows 10 Update Rings – Create Update Ring – Settings. We must select the “Servicing Branch” options according to your requirements. Feature update deferral period (days) is another set we want to set up as part of the Create Update Ring policy.
- For example:- If we set Service Branch = CB and Feature update deferral period (days) = 0 days, then the device will get the Windows 10 1709 updates on the 0 days of the release.
- As I mentioned in the above paragraph, there are two types of Servicing Branches for Windows 10: Semi-Annual Targeted and Semi-Annual.
- Select the CB servicing branch (Semi-Annual Targeted) to set the devices for the first wave of deployment of Windows 10 feature upgrades. The latest Windows 10 1709 Fall Creators update is released only for the Semi-Annual Targeted branch.
How Do Windows 10 Update Rings Work?
Windows 10 update rings work flawlessly under the hood. I have not uploaded Windows 10 1709 ISO or files to Intune to deliver the updates to the devices. Intune helps to set up 2 MDM policies in Windows 10 1607 or later devices.
So, Devices, are you getting the Windows 10 feature update binaries from any other Microsoft cloud service? Windows 10 devices are getting these feature update content/binaries from Windows Update for Business (WUfB).
Another essential feature of Windows 10 is Delivery Optimization. Delivery optimization helps to find the binaries from the peer devices. These peer devices could be either from the same network or the internet.
Windows 10 Update Ring MDM Policies?
The following are the two MDM policies that Intune sets on Windows 10 devices. Intune Windows 10 Quality Update Policies.
CB/CBB Options:- MDM for version 1607 and above: MDM for version 1607 and above: ../Vendor/MSFT/Policy/Config/Update/BranchReadinessLevel \Microsoft\PolicyManager\default\Update\BranchReadinessLevel
Deferral Period Days:- MDM for version 1607 and above: ../Vendor/MSFT/Policy/Config/Update/DeferFeatureUpdatesPeriodInDays \Microsoft\PolicyManager\default\Update\DeferFeatureUpdatesPeriodInDays
Windows 10 Upgrade End User Experience
The following video delivers the Windows 10 1709 fall creator update through Windows Update for Business. The next video will give you an end-to-end experience for the Windows 10 1709 fall creators’ upgrade process via Software Update for Business (WUfB).
As you can see in the video, the Windows 10 device is in the CB (Semi-Annual Target) channel and the differed period policy is set to zero days—Intune Windows 10 Quality Update Policies.
References
- What’s new for IT pros in Windows 10, version 1709
- How to Setup Windows 10 Software Update Policy Rings in Intune Azure Portal
- Configure Windows Update for Business
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.